Blockchain Hash Function
Last Updated :
13 Oct, 2022
A hash function is a mathematical function that takes an input string of any length and converts it to a fixed-length output string. The fixed-length output is known as the hash value. To be cryptographically secure and useful, a hash function should have the following properties:
- Collision resistant: Give two messages m1 and m2, it is difficult to find a hash value such that hash(k, m1) = hash(k, m2) where k is the key value.
- Preimage resistance: Given a hash value h, it is difficult to find a message m such that h = hash(k, m).
- Second preimage resistance: Given a message m1, it is difficult to find another message m2 such that hash(k, m1) = hash(k, m2).
- Large output space: The only way to find a hash collision is via a brute force search, which requires checking as many inputs as the hash function has possible outputs.
- Deterministic: A hash function must be deterministic, which means that for any given input a hash function must always give the same result.
- Avalanche Effect: This means for a small change in the input, the output will change significantly.
- Puzzle Friendliness: This means even if one gets to know the first 200 bytes, one cannot guess or determine the next 56 bytes.
- Fixed-length Mapping: For any input of fixed length, the hash function will always generate the output of the same length.
How do Hash Functions work?
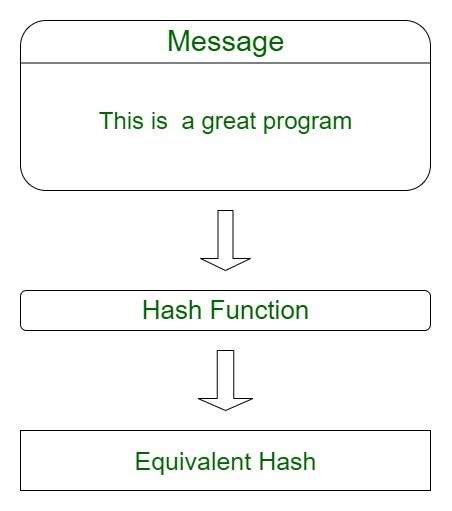
The hash function takes the input of variable lengths and returns outputs of fixed lengths. In cryptographic hash functions, the transactions are taken as inputs and the hash algorithm gives an output of a fixed size.
The below diagram shows how hashes work.
Types of Cryptographic Hash Functions
There are several different classes of hash functions. Some of the popular classes are:
1. RACE Integrity Primitives Evaluation Message Digest (RIPEMD): This set includes RIPEMD, RIPEMD-128, RIPEMD-160, RIPEMD-256, RIPEMD-320.
- Out of these RIPEMD-160 is the most common.
- The original RIPEMD-128 is based on the design principles used in MD4.
- The RIPEMD-256 and 320 have fewer chances of the accidental collision but do not have higher levels of security as compared to RIPEMD-128 and RIPEMD-160.
2. Message-Digest Algorithm: This family comprises hash functions MD2, MD4, MD5, and MD6.
- MD5 is the most widely used cryptographic hash function.
- It is used to generate a 128-bit digest from a 512-bit string broken down into 16 words composed of 32 bits each.
- Ronald Rivest designed this algorithm in 1991 to use for digital signature verification.
- These are no longer considered cryptographically secure methods and should not be used for cryptographic authentication.
3. BLAKE2: It was announced on December 21, 2012.BLAKE2 is a cryptographic hash function based on BLAKE, designed with the aim to replace MD5 and SHA-1 algorithms in applications requiring high performance in software. It provides better security than SHA-2 and is similar to that of SHS-3. It provides the following features:
- It provides immunity to length extensions.
- It removes the addition of constants to message words.
- It simplifies padding and reduces the number of rounds from 16 to 12.
4. BLAKE3: It was announced on January 9, 2020. BLAKE3 is a cryptographic function based on Bao and BLAKE2. It is a few times faster than BLAKE2. This algorithm provides many features like parallelism, XOF, KDF, etc.
5. Whirlpool: It is a cryptographic hash function, first described in 2000. It is a modified version of the Advanced Encryption Standard (AES). Whirlpool produces a hash of 512 bits.
6. Secure Hashing Algorithm: The family of SHA comprises four SHA algorithms: SHA-0, SHA-1, SHA-2, and SHA-3.
- SHA-0 is a 160-bit hash function that was published by the National Institute of Standards and Technology in 1993.
- SHA-1 was designed in 1995 to correct the weaknesses of SHA-0. In 2005, a method was found to uncover collisions in the SHA-1 algorithm due to which long-term employability became doubtful.
- SHA-2 has the following SHA variants, SHA-224, SHA-256, SHA-384, SHA-512, SHA-512/224, and SHA-512/256. It is a stronger hash function and it still follows the design of SHA-1.
- In 2012, the Keccak algorithm was chosen as the new SHA-3 standard.
- SHA-256 is the most famous of all cryptographic hash functions because it’s used extensively in blockchain technology. The SHA-256 Hashing algorithm was developed by the National Security Agency (NSA) in 2001.
Uses of Hash Functions in Blockchain
The blockchain has a number of different uses for hash functions. Some of the most common uses of the hash function in blockchain are:
- Merkle Tree: This uses hash functions to make sure that it is infeasible to find two Merkle trees with the same root hash. This helps to protect the integrity of the block header by storing the root hash within the block header and thus protecting the integrity of the transactions.
- Proof of Work Consensus: This algorithm defines a valid block as the one whose block header has a hash value less than the threshold value.
- Digital signatures: Hash functions are the vital part of digital signatures that ensures data integrity and are used for authentication for blockchain transactions.
- The chain of blocks: Each block header in a block in the blockchain contains the hash of the previous block header. This ensures that it is not possible to change even a single block in a blockchain without being detected. As modifying one block requires generating new versions of every following block, thus increasing the difficulty.
Thus, it can be concluded hash functions are a vital part of the blockchain technology used to protect the integrity and immutability of the data stored on the blockchain.
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...