Finding Exploit offline using Searchsploit in Kali Linux
Last Updated :
24 Dec, 2020
SearchSploit is a command-line search tool for Exploit-DB that allows you to take a copy of the Exploit Database with you. Searchsploit is included in the Exploit Database repository on GitHub. SearchSploit is very useful for security assessments when you don’t have Internet access because it gives you the power to perform detailed offline searches for exploits in the saved Exploit-DB.
Installing SearchSploit – To run SearchSploit in Kali Linux, open the terminal and type “searchsploit” to run SearchSploit as “exploitdb” package is already included in Kali Linux. However, if you are using the Kali Light variant or your custom-build ISO then you can install SearchSploit manually using the below-mentioned command.
sudo apt update && sudo apt -y install exploitdb
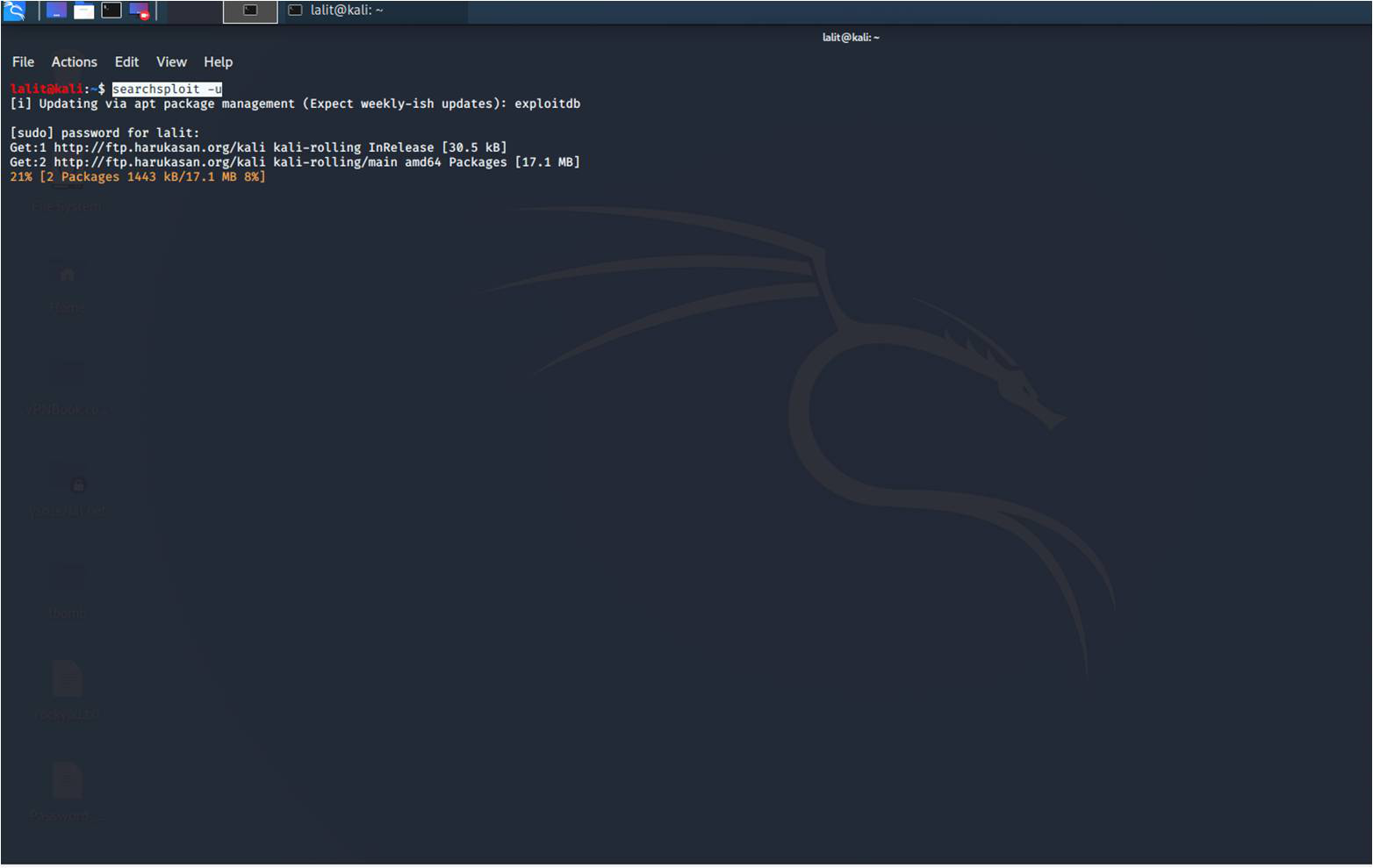
Updating SearchSploit: In order to update SearchSploit, run the following command:
searchsploit -u
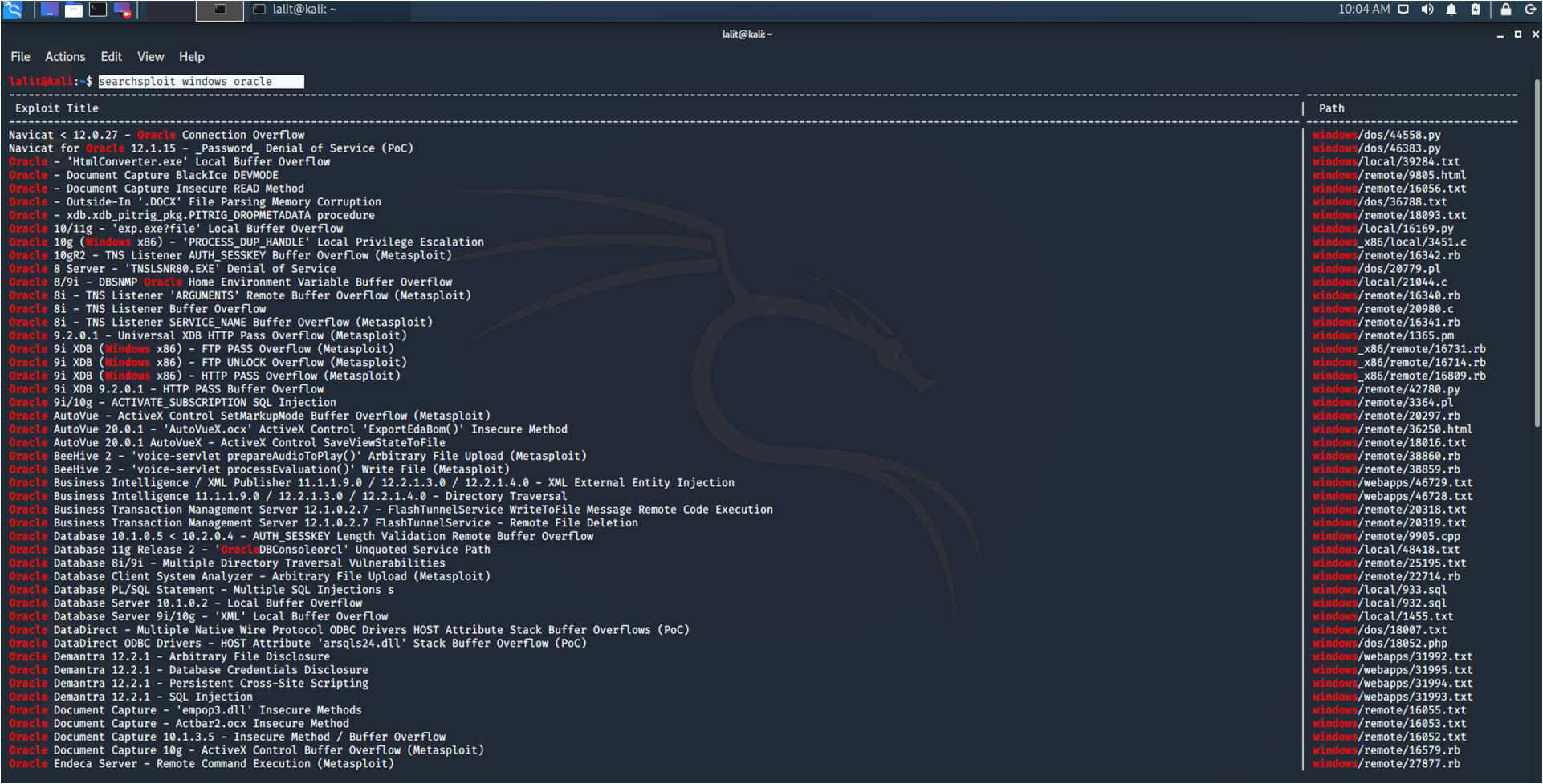
Using SearchSploit:
1. Basic Search – You can add any number of search terms you wish to look for. In the below image, we are searching for exploits containing the term “oracle” and “windows”.
In case you need help just type “searchsploit -h” in the terminal. By using -h, you can see all the options and features that are available to you:
2. Title Searching in SearchSploit: If you are performing Basic Search, searchsploit will check for both the path and the title of the exploit. Searches can be restricted to the titles by using the -t option as follows:
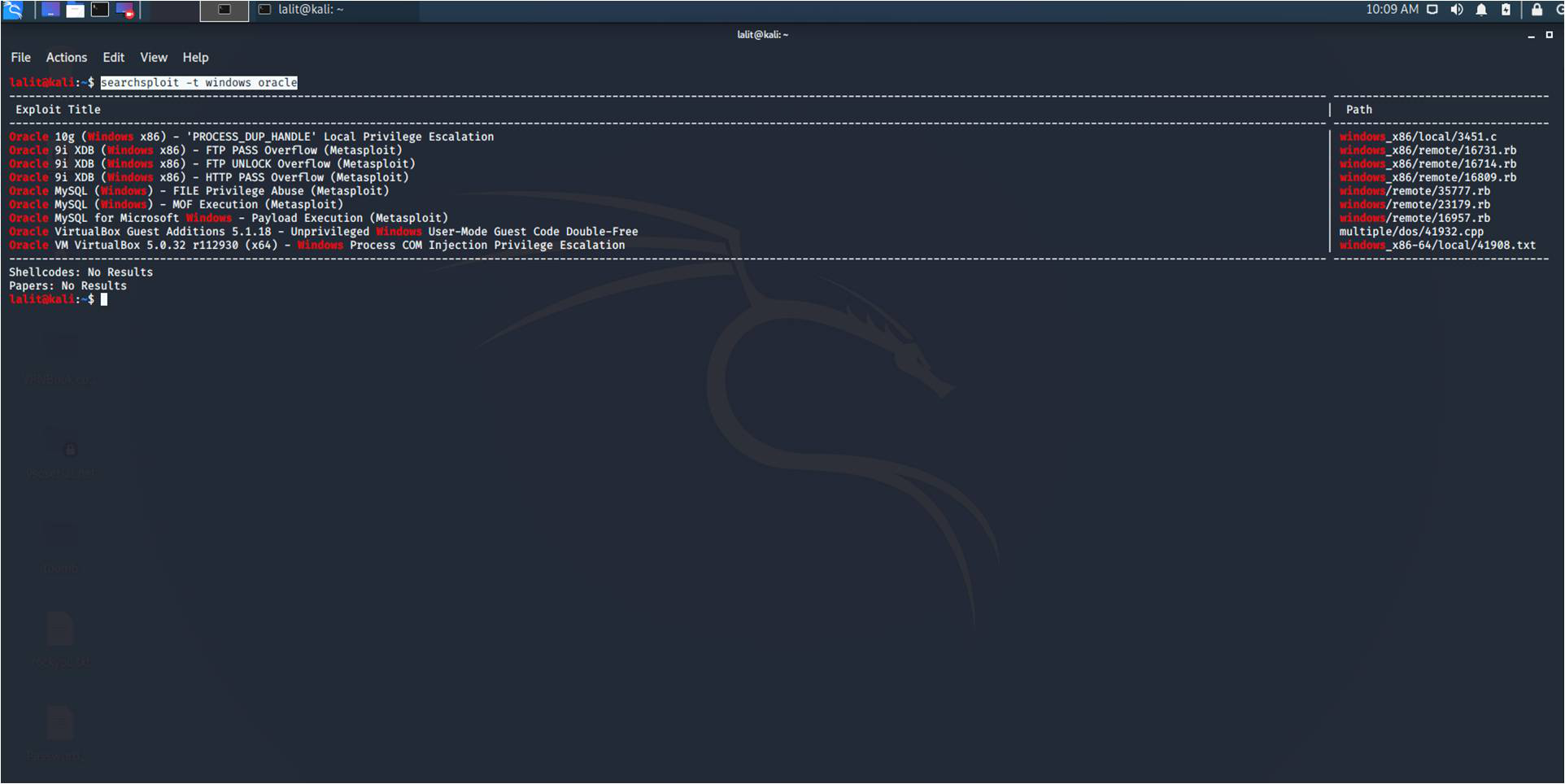
In the above search, we are looking for the exploits related to Oracle based on Windows OS.
3. Copying Exploit to Clipboard and Directory: If you want to copy the exploit to clipboard use ‘-p’. For example – ” searchsploit -p XYZ ” , here XYZ is the exploit ID. If you want to copy the exploit in your current working directory use ‘-m’. For example – ” searchsploit -m XYZ “, where XYZ is the exploit ID.
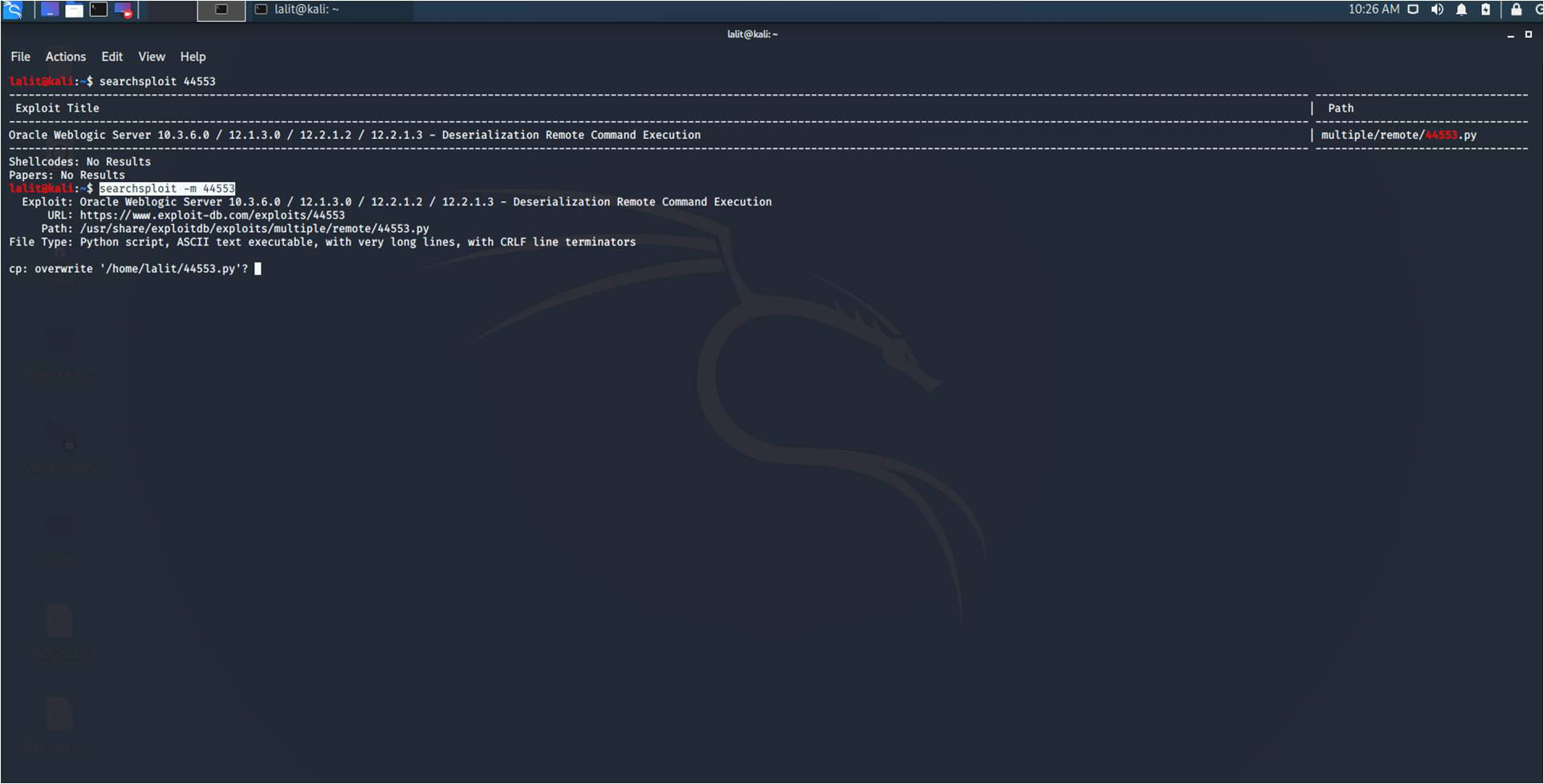
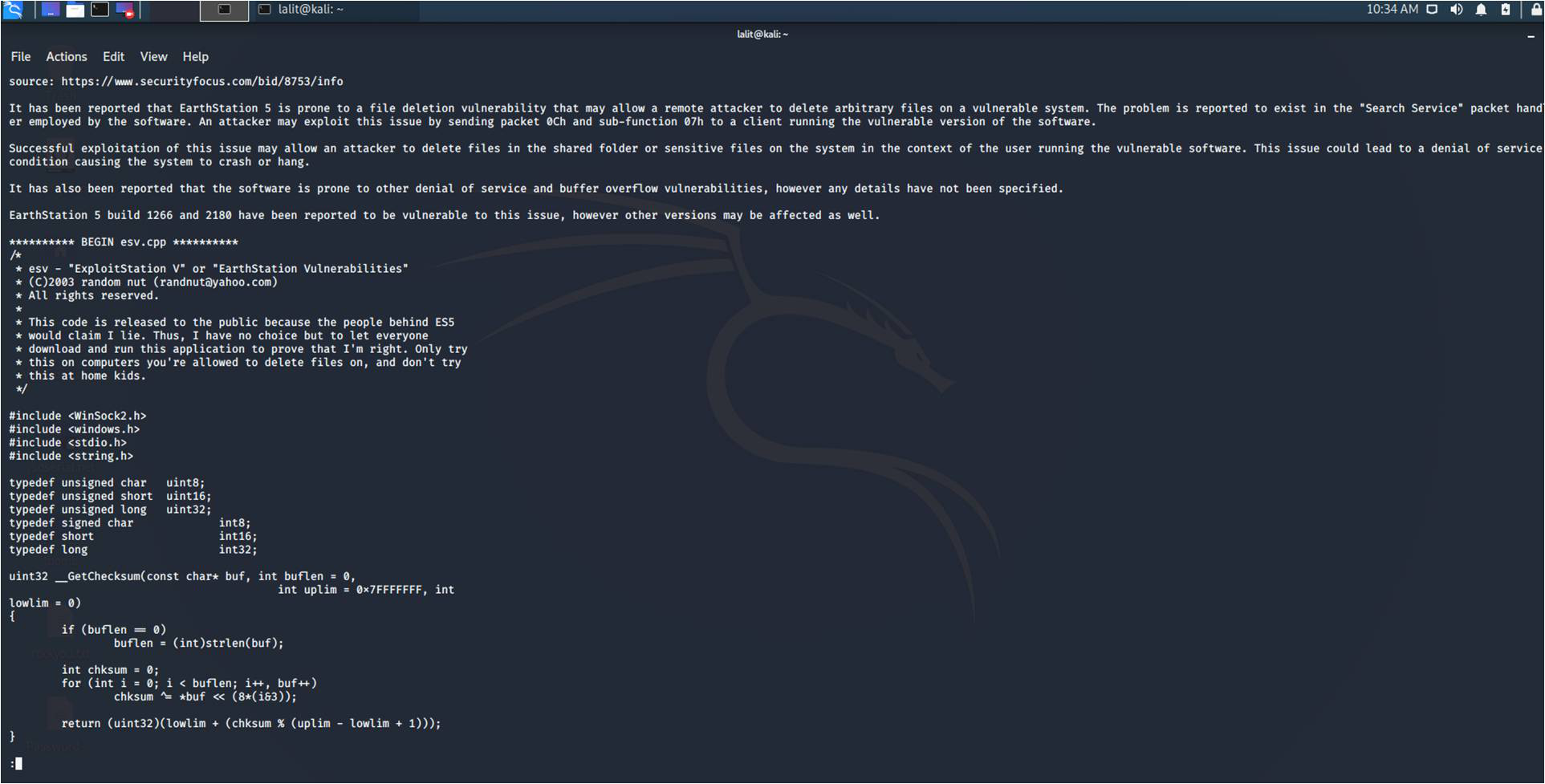
4. Examine an Exploit: If you want to examine an exploit or want to study an exploit, use ‘–examine’. For example – “searchsploit XYZ –examine” , where XYZ is the exploit ID.
5. Eliminate Unwanted Results: If you want to eliminate unwanted results from your search simply use ‘–exclude’. You can also remove multiple terms by separating the terms with a “|” (pipe). For example – searchsploit –exclude “PoC”.
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...