Find All Failed SSH login Attempts in Linux
Last Updated :
02 Jun, 2023
SSH Server provides us with a secure encrypted communications channel between two untrusted hosts over an insecure network. Still, we cannot say for sure that it is secure. It is generally very susceptible to many kinds of password-guessing and brute-forcing attacks. By actively monitoring these failed login attempts one can easily find the unauthorized access that is attempted on our system. In this article, we are going to discuss different ways to identify the failed SSH login attempts in Our Linux System.
The syntax for enabling, starting, and checking the status of the SSH Service
sudo systemctl enable ssh
Enabling SSH service
sudo systemctl start ssh
Starting SSH service
sudo systemctl status ssh
Checking SSH service status
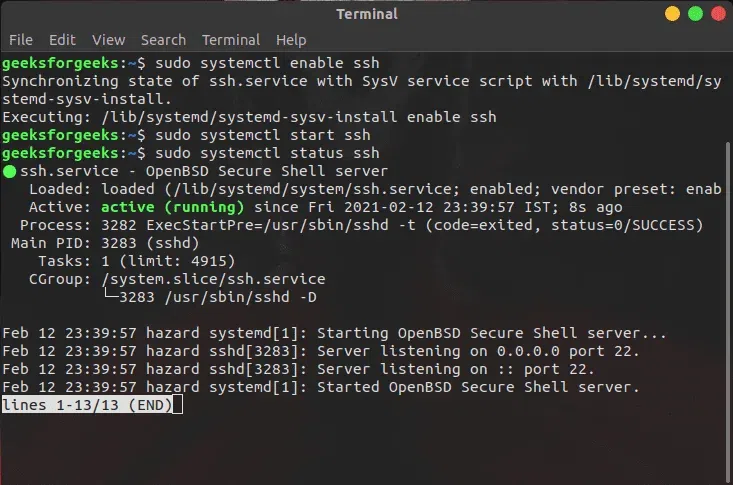
SSH Service Actively running.
Checking SSH log Files in Linux
If we talk about Linux system which typically logs all the login attempts in a log file. If we examine this log file, we can easily identify the failed login attempts that are made. The path of the log file can be different in different Linux distributions, but in geranyl common location are ‘/var/log/auth.log’ or ‘/var/log/secure’. To view the contents of the log file, we can use `cat` or `less` command.
cat /var/log/auth.log
or
less /var/log/auth.log
The Log file contains valuable information like
- Ip address
- date
- time
- user attempting to log in
Note: Failed login attempts are usually marked with a “Failed password” or “invalid user” message.
Using `grep` and `cat` command for searching
The `grep` command is a powerful toll for searching in a pattern in text file. We can be more specific in searching the text file by utilizing regular expressions in it.
For Example:
Using `grep` to find failed SSH login attempts.
Syntax:
grep "Failed password" /var/log/auth.log

grep command to find logs
As we can see it displays all the lines containing the phrase “Failed Password” in the auth.log file. our search can be more refined according to the user by using multiple desired conditions.
For Example:
Using `cat` with `grep` command
Syntax:
cat /var/log/auth.log | grep "Failed password"
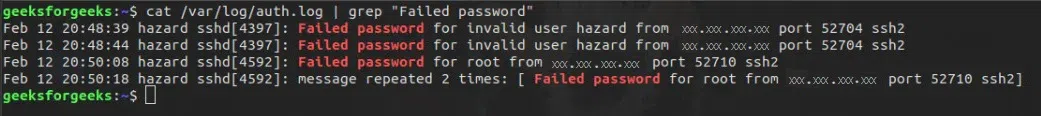
cat and grep command to find logs
Additional Information Failed SSH login Attempts
If we want to gather more details about the failed logins attempts that are made, we can use `egrep` command with the desired pattern.
Syntax:
egrep "Failed|Failure" /var/log/auth.log
We will get a comprehensive view of all failed login attempts, including various error messages or failure reasons
Extracting IP Address
If want to get IP addresses and the number of failed logins attempts, we can combine `grep`, `awk`, `uniq` and `sort` command to see the desired result.
Syntax:
grep "Failed password" /var/log/auth.log | awk '{print $11}' | uniq -c | sort -nr
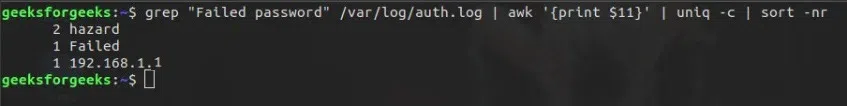
extracted filter out duplicate IP
As a result, we have extracted filter out duplicate IP addresses and counts the occurrence and get it in descending order.
Using Systemd’s journaltcl
There is another way to get SSH login attempts by using the `Systemd daemon’s journaltcl` command.
Syntax:
journalctl _SYSTEMD_UNIT=ssh.service | egrep "Failed|Failure"

journalctl _SYSTEMD_UNIT=ssh.service | egrep “Failed|Failure”
As a result, we can retrieve relevant log entries related to failed login attempts.
Checking Settings
If we want to fine-tune the settings for handling failed loging attempts we can review the /etc/pam.d/common-auth file. The /etc/pam.d/password-aut file can be checked for setting related to failed login attempts and tempry account locking.
cat /etc/pam.d/password-auth
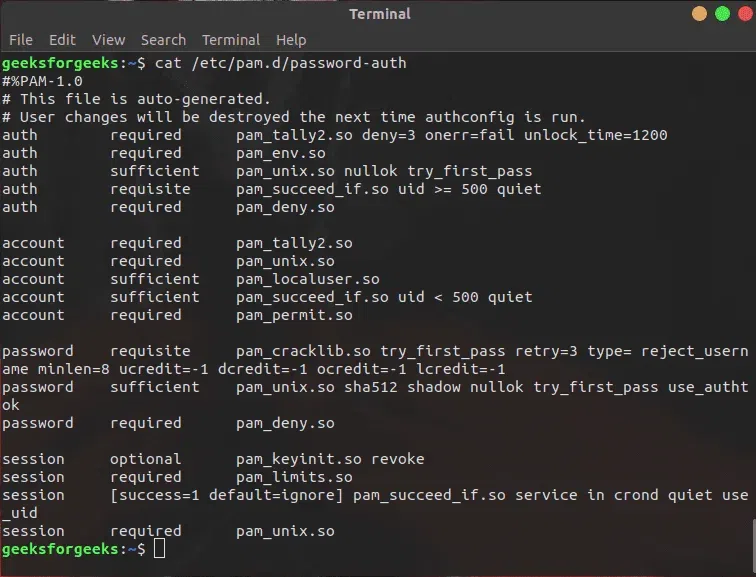
cat /etc/pam.d/password-auth
For Example:
We can also adjust the threshold for failed login attempts before our account is temporarily locked by modifying the following line in the file.
Syntax:
auth required pam_tally2.so deny=3 unlock_time=360
This line in result will sets the account lockout after the three failed login attempts and here 360 means second which is 6 min lockout duration
Conclusion
In this article we have discussed how we can identify and monitor failed SSH Login attempts in Linux. Which is important for a user to know for maintaining system security. We have discussed different ways to find the failed login attempts `grep`, `cat` and `egrep` etc. Overall, we can say that by actively monitoring failed SSH login attempts, we can enhance system security and prevent potential threats.
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...