Types of Authentication Protocols
Last Updated :
11 Jul, 2022
User authentication is the first most priority while responding to the request made by the user to the software application. There are several mechanisms made which are required to authenticate the access while providing access to the data. In this blog, we will explore the most common authentication protocols and will try to explore their merits and demerits.
Kerberos is a protocol that aids in network authentication. This is used for validating clients/servers during a network employing a cryptographic key. It is designed for executing strong authentication while reporting to applications. The overall implementation of the Kerberos protocol is openly available by MIT and is used in many mass-produced products.
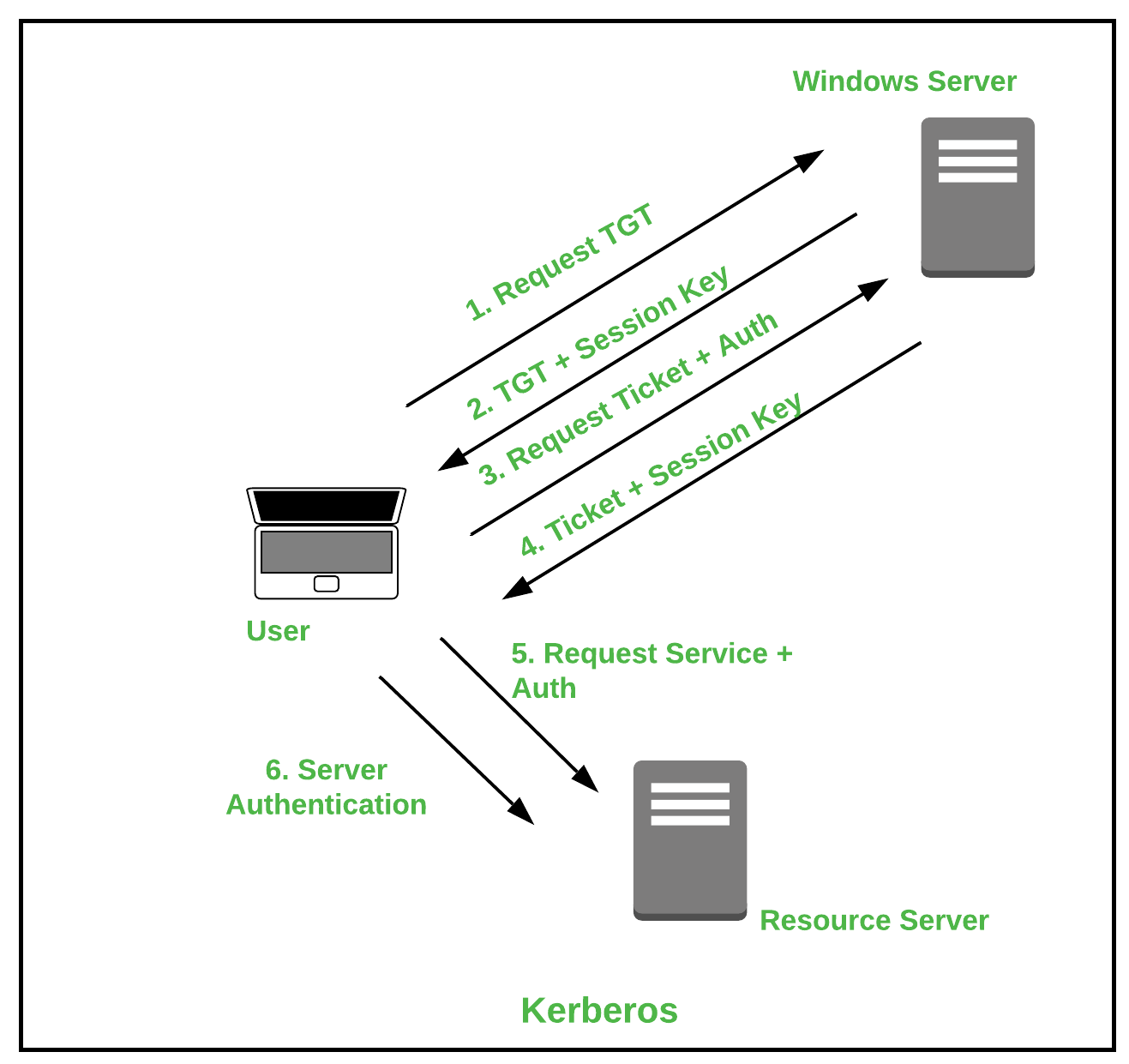
Some advantages of Kerberos :
- It supports various operating systems.
- The authentication key is shared much efficiently than public sharing.
Some disadvantages of Kerberos :
- It is used only to authenticate clients and services used by them.
- It shows vulnerability to soft or weak passwords.
2. Lightweight Directory Access Protocol (LDAP) :
LDAP refers to Lightweight Directory Access Protocol. It is a protocol that is used for determining any individuals, organizations, and other devices during a network regardless of being on public or corporate internet. It is practiced as Directories-as-a-Service and is the grounds for Microsoft building Activity Directory.
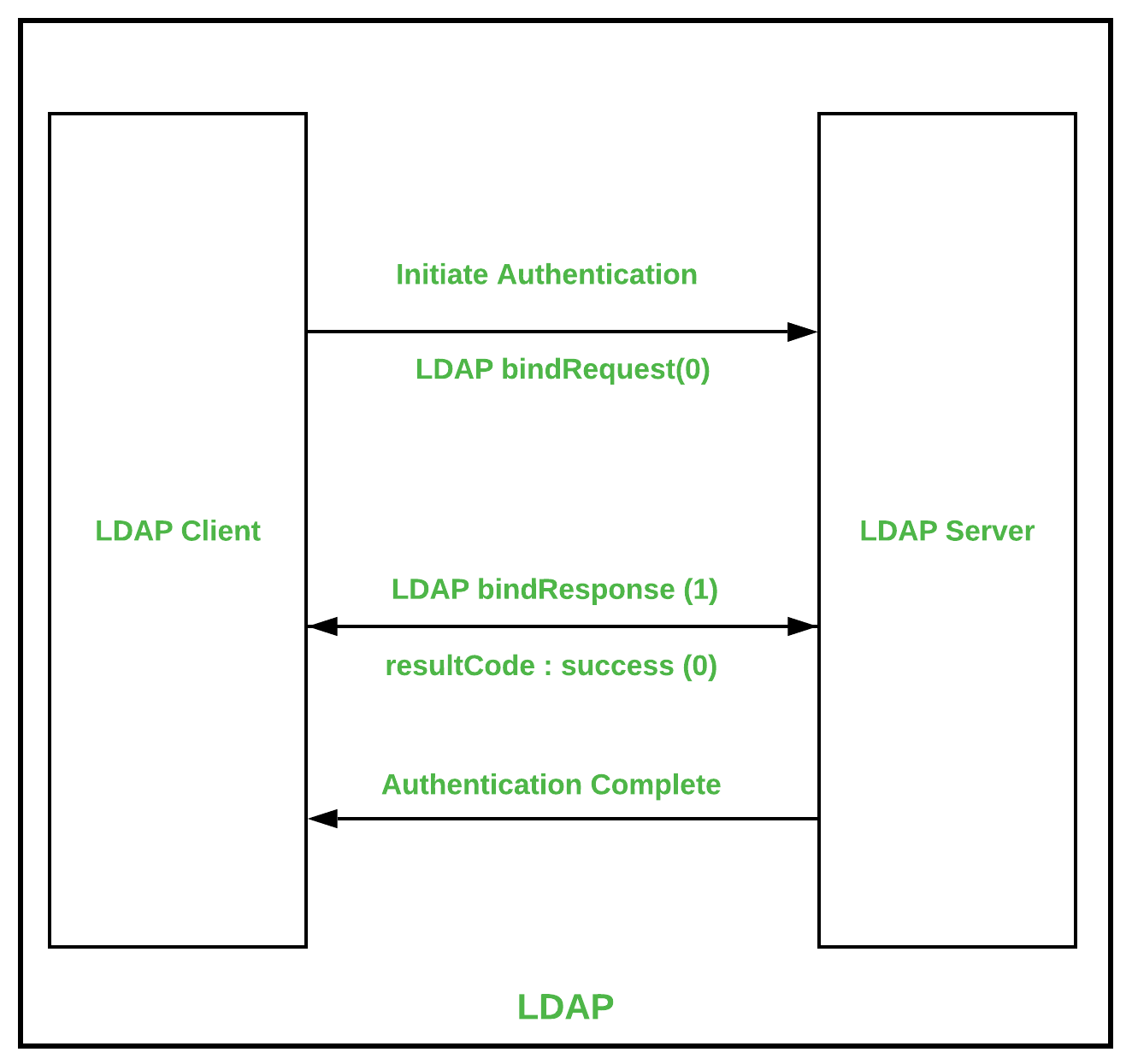
Some advantages of LDAP :
- It is an automated protocol which makes it modernizing easier.
- It supports existing technologies and allows multiple directories.
Some disadvantages of LDAP :
- It requires the experience of deployment.
- The directory servers are required to be LDAP obedient for deployment.
3. OAuth2 :
OAuth as the name suggests it is an authorization framework that promotes granting limited access to the user on its account through an HTTP service. When a user requests access to resources an API call is made and after the authentication token is passed.
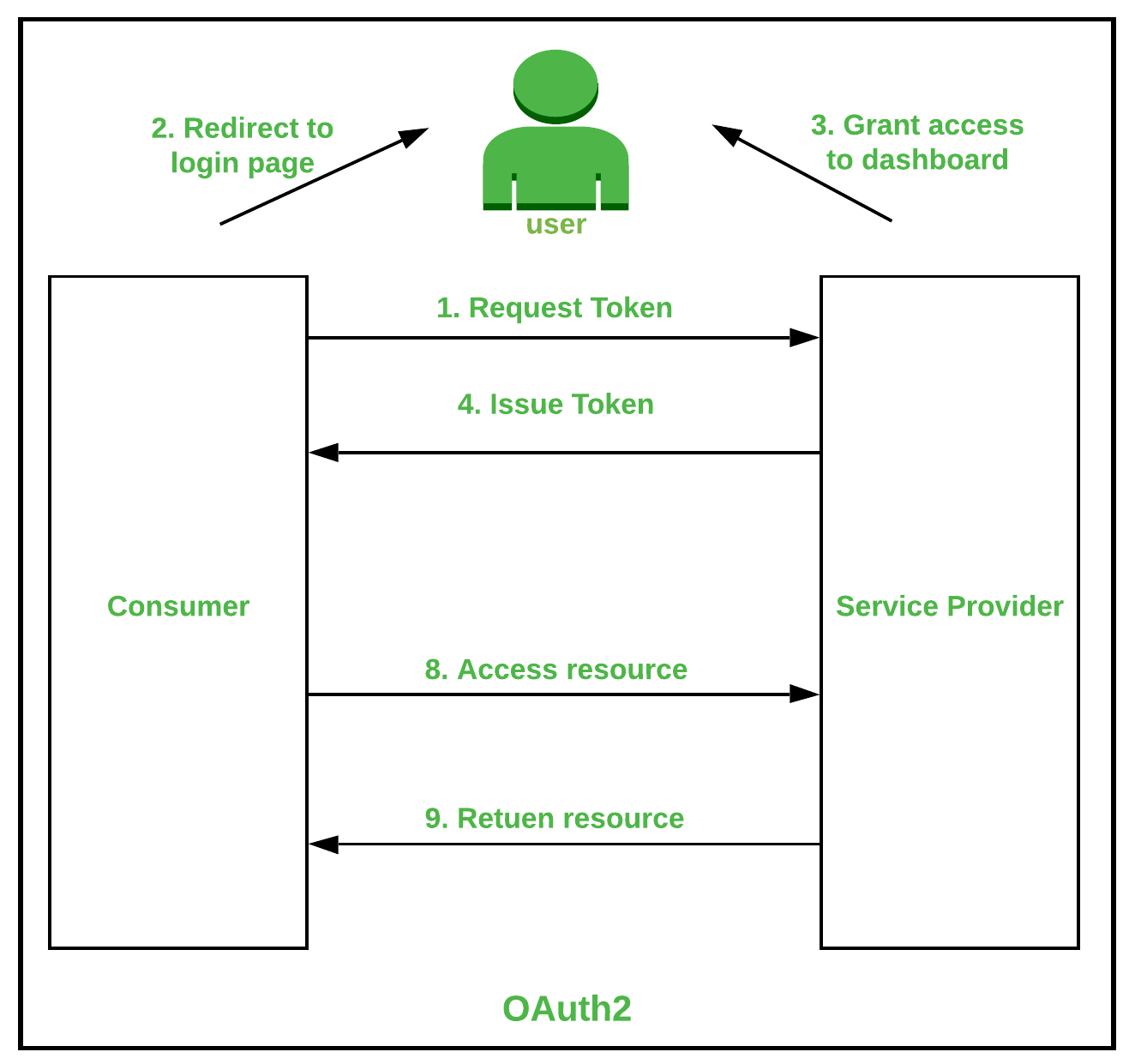
Some advantages of OAuth2 :
- It is a simple protocol and is easy to implement.
- It provides server-side authorization of code.
Some disadvantages of OAuth2 :
- It is vulnerable to manage different sets of code.
- It shows serious effects on sites connected to another affected system.
4. SAML :
SAML stands for Security Assertion Markup Language which is based on XML-based authentication data format which provides the authorization between an identity provider and service provider. It serves as a product of the OASIS Security Services Technical Committee.
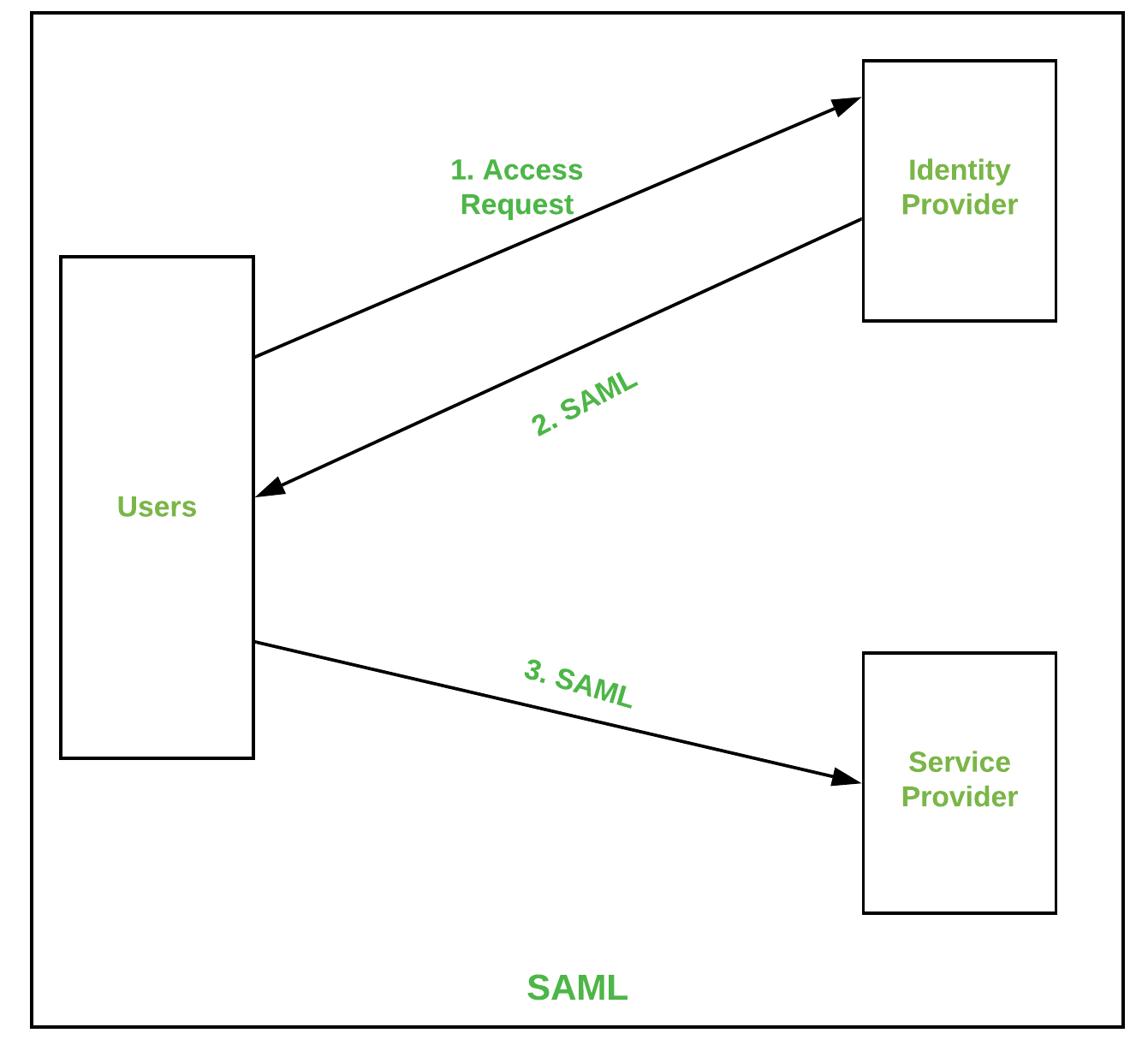
Some advantages of SAML :
- It reduced the administrative costs for the end-users.
- It provides a single sign-in for authenticating across service providers.
Some disadvantages of SAML :
- It is dependent on the identity provider.
- All the data is managed in a single XML format.
5. RADIUS :
RADIUS stands for Remote Authentication Dial-In User Service. It is a network protocol that provides sufficient centralized Authentication, Accounting, and Authorization for the users that use and network services. The functioning of the protocol occurs when the user requests access to network resources, where the RADIUS server encrypts the credentials which are entered by the user. After this, the user credentials are mapped through the local database and provide access.
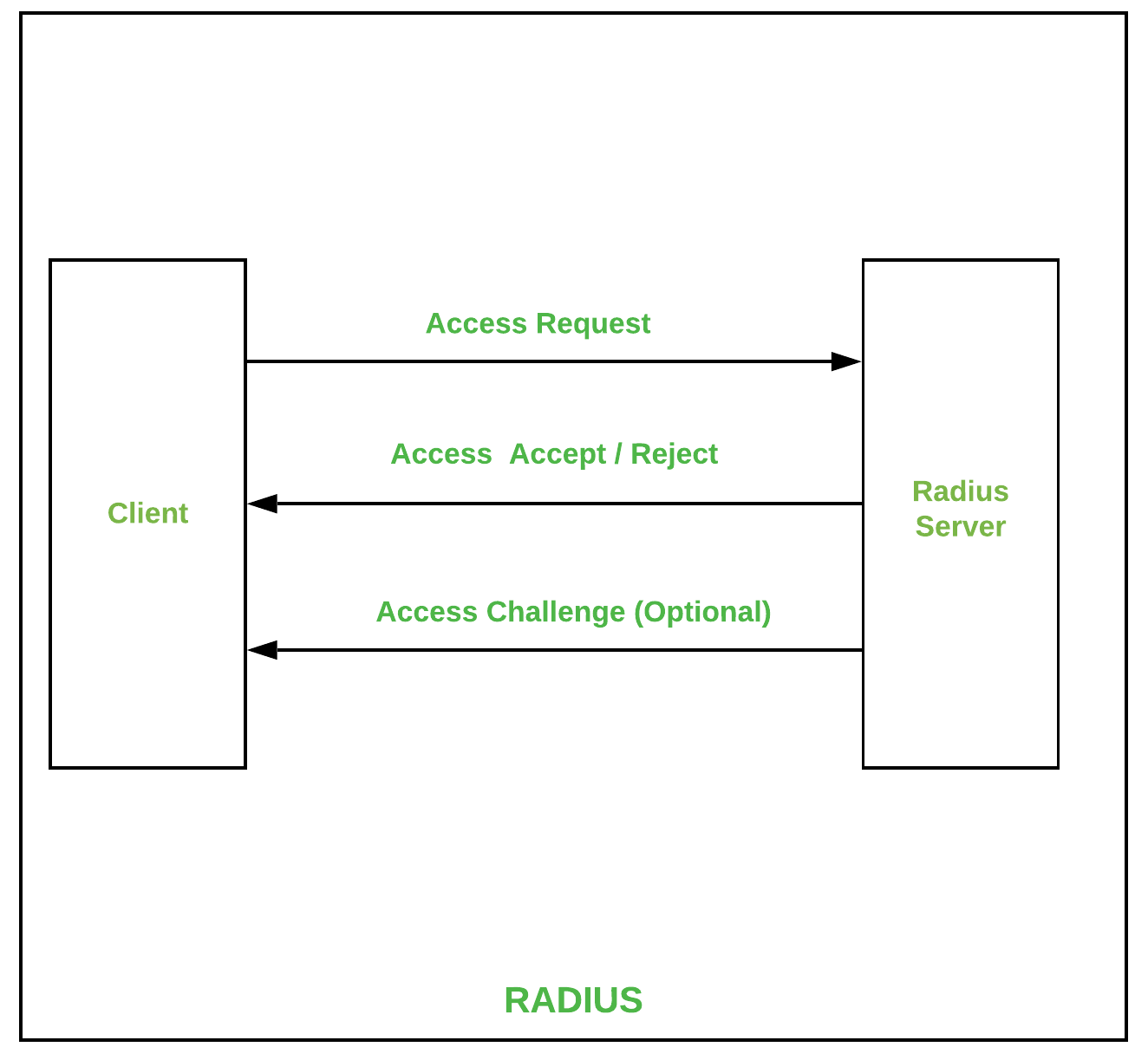
Some advantages of RADIUS :
- It is a great mechanism for providing multiple access for Admins.
- It provides a unique identity to each user in a session.
Some disadvantages of RADIUS :
- Initial implementation for this mechanism is hard on hardware.
- It has a variety of models that may require a special team which is cost consuming.
Differentiating between the protocols will not make justice to the protocols because it depends on the use of the application and for what purpose it is being used.
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...