What is DNS Spoofing ?
Last Updated :
31 Mar, 2022
Have you ever stumbled across emails and websites that seem suspicious but you aren’t sure if it has been authenticated or not? I am sure we all have seen an email or a website that has all of the signs of being suspicious and our spidey senses go off. I am writing this to help explain what you saw and the potential dangers of what you could’ve been a victim of. This article is about DNS spoofing.
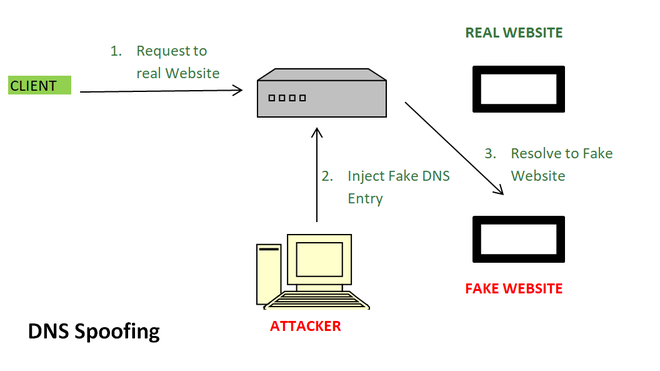
DNS spoofing or DNS cache poisoning is an attack in which altered DNS records are used to redirect users or data to a fraudulent website or link that is camouflaged as the actual destination. An example of this would be when you go to facebook.com on an unsecured network with no antivirus. If someone happens to be sniffing on your open port or has already done a man-in-the-middle attack, then they are able to corrupt the DNS records. Therefore, redirecting you to a fake Facebook page that is a replica of the official login page. When you type in your username and password they will be able to steal your login credentials and inject a virus or worm into your IP address.
So going more into the details of what DNS spoofing is in the simplest of terms. Every computer and device has an IP address and every website has a domain name(www.google.com) that allows internet users to visit the page. The DNS or domain name system then maps out and plots out the domain name that users enter to the appropriate IP address to properly route the traffic. The sorting and routing is handled by the DNS servers. DNS poisoning is when a hacker injects a corrupt piece of DNS instructions into the DNS server and takes advantage of an exploit in the process of redirecting traffic. The corrupt piece of DNS data that is sent to the DNS server is now redirecting traffic to a fake login page that looks exactly like the official page. When the users enter their credentials, it is either being recorded through a keylogger or being sent in a .txt file to the hacker so they have the information stored in an alternate location.
A way to interpret this process and vulnerability is to look at it in the form of something you can relate to. Let’s say you are going to your favorite grocery store to get groceries. You have to get rice, canned beans, some bread, deli meat, etc. So you get to the grocery store and you see that obviously there are aisles where different items are located(this can be related to the many websites out there and domain names). So you grab all of your items and go to the checkout lines. Since all of the checkout lines are full you will usually have an attendant directing people to the next available opening in a checkout aisle(this is the DNS servers directing and routing all traffic to the websites). So you are directed to the next aisle and checkout and pay for all of your items but the cashier working there was not really an employee and has stolen everyone’s credit card information in that line(this is the hacker injecting a corrupt DNS entry into the DNS servers and redirecting users to the fake login page and stealing their login credentials).
Like Article
Suggest improvement
Share your thoughts in the comments
Please Login to comment...